|
Our country is just one nation that makes up the rest of the world. And considering how many countries there are coexisting with us (albeit not always peacefully), it’s hard to maintain law and order all the time. It’s what governments are for. Well, aside from collecting taxes, the government is tasked to maintain peace and order and manage the affairs of the state. It’s a lot of work actually and can’t be done by a single individual. It’s why there are different agencies that enforce the law and some who act like Sherlock Holmes and try to put a stop to criminals before they even strike.
(Via: https://www.yahoo.com/tech/cia-hacks-computers-aren-t-even-connected-internet-190134195.html) Given that the CIA’s work is based on gathering foreign intelligence, it’s a given that they have to be computer-savvy because the world is more digital than ever. They have to be crafty and resourceful in gathering foreign data that may be of value to the government especially when it’s the national security on the line. Terror attacks happen more often today than it did in the past and we don’t want more Americans to die in the hands of heartless terrorists who only want to cause chaos and disrupt the natural order of the world. Wikileaks just enlightened the world how smart CIA agents are because they can even hack computers that are offline, meaning these PCs aren’t even turned on in the first place.
(Via: https://fossbytes.com/brutal-kangaroo-malware-cia-offline-computers/) While the rest of innocent and law-abiding Americans citizens don’t have anything to worry about this computer hacking ability of the Central Intelligence Agency, foreign individuals who have evil plans for anyone living in America or any American citizen should be very afraid because the CIA will find a way to get you and you can count on them to hack your computer first before they apprehend you, because they will. The CIA hacks offline systems through the malware, Brutal Kangaroo. You may not have to worry about Brutal Kangaroo if you are not a terrorist or a criminal yourself but you aren’t immune to malware that is spreading all over the web today. When you get hit by this bug, you lose access to important data and you don’t want that to happen. Data recovery may be your last resort although having backup data is a good precaution. Learn more about data recovery here: http://www.harddriverecovery.org/clean_room.html. For an older system like RAID, this http://www.harddriverecovery.org/server-recovery/ may come in handy. The CIA’s Superior Computer-Hacking Skills was originally seen on HDRG via http://www.harddriverecovery.org/blog/the-cias-superior-computer-hacking-skills/
0 Comments
The world is run by computers. It is the reality of our times these days. Almost every nation has centralized their operations and relies heavily on digital data in their every affair. It has transformed the delivery of basic services into a smooth and efficient system that gets the job done every time. Unfortunately, like any form of technology, criminals have found their way to make money from it and this has put a risk countless computer servers all over the world from costly malware that are meant to cripple your system and even your life (and put your business on hold).
(Via: https://www.ft.com/content/348d4f7a-3808-11e7-821a-6027b8a20f23) It is unusual for Microsoft to provide support for older software versions that have been released ages ago but they made an exemption this time considering 7% of the computers all over the world still run on Windows XP today and were also affected by the recent cyber attacks to prevent the malware from spreading further. If not protected, this ransomware can cripple your system by locking it and its keyboard and you won’t be able to access all the data stored on your hard drive. What’s even more stressful about the recent attack is that it affected computer servers of various organizations, thereby crippling government institutions and companies in one go.
(Via: https://www.macrumors.com/2017/05/07/handbrake-app-security-warning-servers-hacked/) Whether you are using a Mac PC or a Windows one, you are not safe from these hackers. It is especially more costly for business owners who use several if not hundreds to thousands of PCs running on the same server. It is what happened during the recent WannaCry attack that crippled various industries both public and private. Cyber criminals have upped their A-game and will go to extreme lengths just to wreak havoc and get the world’s attention (not to mention the ransom money in the form of bitcoins). Their modus is simple. They introduce the malware into your system in the form of malicious email attachments disguised as a regular email you typically get from family, friends, or co-workers. Upon opening, the malware gets into your system and the attacker locks your PC and keyboard, so you can no longer access anything on your computer and your data held as a hostage. In times like this, you can only hope for a miracle remedy for this situation like the genius 22-year old tech wizard who found the kill switch for WannaCry. However, there are other instances where you may end up losing your precious data such as the very common hard drive failure experienced by most businesses at some point in time. Check this link http://www.harddriverecovery.org/raidcenter/dell_poweredge_data_recovery.html for Dell server data recovery and this one http://www.harddriverecovery.org/raidcenter/hp-proliant-data-recovery.html for the HP Proliant server recovery. If you do experience these issues, don’t hesitate to contact us for professional help. The following blog post Malware Continues To Threaten Computer Servers All Over The World Find more on: HDRG via http://www.harddriverecovery.org/blog/malware-continues-to-threaten-computer-servers-all-over-the-world/ For an ordinary person, we likely hear crickets chirping when we hear others talk extensively about computers using unheard of computer jargons. Understanding many of these computer concepts and terms isn’t an easy feat, so we often just stick to what we know best: social media and the Internet.
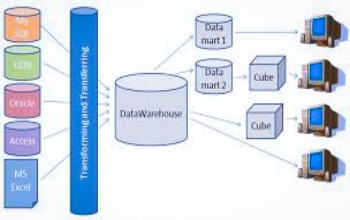
(Via: http://www.computerweekly.com/blog/CW-Developer-Network/What-is-data-warehouse-automation) Simply put, data warehouse automation is a process wherein you automate and accelerate the development cycles of data warehouse without compromising consistency and quality. In short, you just automate the entire process. This is especially helpful in big enterprises that handle big data in their daily operations to let you do more things quite faster without spending a fortune on it.
(Via: https://hbr.org/sponsored/2017/05/how-an-online-grocery-platform-could-reshape-retail-as-we-know-it) Although generally used by a local business, an online grocery system is the perfect smaller-scale example of data warehouse automation at work. They have an extensive yet efficient data management system in place to keep track of inventory, supplier details, customer details and many others. It ensures the grocers move the items on time to gain profits and cut down on losses from spoiled produce.
(Via: http://www.fooddive.com/news/grocery--can-amazon-earn-grocery-dominance-with-more-automation/441720/) Another great example of a company that uses data warehouse automation and became successful at it is no other than Amazon itself. Amazon Fresh provided an avenue for online grocery retailers to reach out to a wider market by selling their products online and providing grocery delivery in America. People these days prefer online shopping rather than going to physical stores and supermarkets to shop for things, which is why companies that can master the process of data warehouse automation may hit the jackpot and thrive where others have failed. Meanwhile, the problem of hard drive failure and the consequent data loss is an issue experienced by almost everyone now and then. When that happens to you and you are using a Seagate hard drive, this link http://www.harddriverecovery.org/seagate-data-recovery.html may help you understand what really happens during its recovery. If you are using an older system, though, like a RAID 10, this post on RAID 10 Data Recovery http://www.harddriverecovery.org/raidcenter/raid-10-data-recovery.html is probably what you are looking for to help you fully understand how to recover lost data using this system. Understanding Data Warehouse Automation was first published on Hard Drive Recovery Group via http://www.harddriverecovery.org/blog/understanding-data-warehouse-automation/ We are now living in a digital world. It means that we use computers in carrying out different tasks or functions whether on a personal basis or not. Almost all homes are equipped with a computer or laptop and have their own Internet or WiFi connection too. The latter is even considered as a necessity these days and no longer a luxury that it once was before smart technology took over the world.
(Via: http://www.popsci.com/remove-malware-from-computer) First and foremost, you must realize that there is a problem and it is pretty obvious too. A warning message will often appear on your screen but there are instances when it does not show at all. Other warning signs to watch out for include crashing applications, lots of pop-ups showing on your browser, and a crawling system.
(Via: https://www.vox.com/new-money/2017/5/12/15632482/ransomware-explained) To protect your PC from ransomware attacks, it is a must to conduct regular checkups. Remember that hackers can only encrypt and steal files saved on your PC, so setting up a backup can save you from a headache caused by such an attack. The only unfortunate thing about this is that most individuals and businesses don’t have a backup plan in place, so they are easily victimized by cyber criminals. Also, it seems that the computers affected were Windows PC because of vulnerability in Windows that wasn’t yet discovered before. Malware is indeed a cause of concern for computer users. However, there is actually more common computer issues that are just as stressful yet don’t usually get the attention it deserves. For instance, hard drive problems are quite common than we would like to admit and everyone is vulnerable to it. If you also don’t backup your files, on say, an external hard drive, you might lose all data saved on your hard drive once it fails. If your hard drive is failing and you need it fixed right away, http://www.harddriverecovery.org/repair-hard-drive.html can help you fix that hard drive and help retrieve all your precious data for you. Meanwhile, if you are still using an old Windows XP or Vista computer, you may likewise encounter a disk read error, this article http://www.harddriverecovery.org/errors/disk_read_error.html can give you tips on how to address this issue. We also offer our expert assistance for a professional service that won’t break the bank. The blog post Protect Your Data From Malicious Malware Find more on: http://www.harddriverecovery.org via http://www.harddriverecovery.org/blog/protect-your-data-from-malicious-malware/ |
About usAffordably priced Irvine, CA area data recovery services provider. Specializing in Macs, Dell, HP and IBM RAID recovery and damaged hard drive recovery services. Also offers Mac and laptop data recovery, as well as all forms of physical and logical data recovery. Archives
November 2019
Categories |




 RSS Feed
RSS Feed
